Archive
How to wrap a user control inside web part using WSP Builder
How to wrap a user control inside web part using WSP Builder
Here , I describe a simple way for wrapping ASP.NET user control inside web part for deployment to SharePoint using WSP builder.
1- Create WSP Project
a- Firstly, you need to have WSP Builder Package to be deployed on your development environment.
b- Open visual studio , from File menu, select New -> Project , Select WSPBuilder from project type pane , in the name box type GSWebpart.
2- Create New WebPart with Feature
a- In visual studio, Right click on GSWebPart Project, and point to Add, and then click New Item…
b- In the Categories pane, click WSPBuilder. In the Templates pane, click Web Part Feature. In the Name box, type ConverterWebPart, and then click OK.
c- In the Feature Settings dialog, type My Web Part for the Title, A web part built using WSPBuilder for the Description and set the Scope to be Site. Click OK.
3- Adding ASP.NET Project Types to the WSPBuilder Project
a- In visual studio, right click on GSWePart Project , select unload project.
b- In visual studio, right click on GSWePart Project , select Edit project.
c- Locate the ProjectTypeGuids element and add the ASP.NET web application project type guid {349C5851-65DF-11DA-9384-00065B846F21}.
d- Save and then close the GSWePart.csproj file.
e- Right-click on the GSWePart project and select Reload Project.
f- Right-click on the GSWePart project and select Properties On the Application tab, change the Target Framework to be .NET Framework 3.5. Save the changes
4- Creating Web User Control
a- In visual studio, right click on Template Folder, then point to add then select new folder , rename it to CONTROLTEMPLATES.
b- Right click on CONTROLTEMPLATES folder , then point to add then select new folder , rename it to GSWebPart.
c- Right-click the GSWebPart folder, select Add then click New Item.
d- In the Categories pane, click Web. In the Templates pane, click Web User Control. Name the control ConverterWebPartUserControl.ascx, and then click Add.
e- Delete the CodeBehind attribute in the ConverterWebPartUserControl.ascx file. Replace the Inherits attribute with GSWebPart. ConverterWebPartUserControl, GSWebPart, Version=1.0.0.0, Culture=neutral, PublicKeyToken=[your PublicKeyToken]. The following code shows the corrected file:
f- <%@ Control Language=”C#” AutoEventWireup=”true” Inherits=” GSWebPart. ConverterWebPartUserControl, GSWebPart, Version=1.0.0.0, Culture=neutral, PublicKeyToken=9410bf5b454f3bbd” %>
g- Open the ConverterWebPartUserControl.ascx file in the designer view. Click the Toolbox, and then add a Label using a drag-and-drop operation. Switch to the code view and rename the ID property to be MyLabel and add “SharePoint” as text property
h- Open the MyWebUserControl.ascx.cs file and the MyWebUserControl.ascx.designer.cs file. Change the namespace to GSWebPart in both files.
5- Wrapping the User Control and Connecting the Properties
This procedure demonstrates how to wrap the user control inside the web part and connect the properties between SharePoint, the web wart and the user control.
To wrap the user control and connect the properties
a- Open the ConverterWebPart.cs file.
b- Within the CreateChildControls() method, delete the single line of code under the // Your code here… comment. Enter code to load the MyWebUserControl, assign the value of MyProperty to the DisplayText property of the control and then add the control to the web part’s Controls collection. The code below demonstrates how to do this:
// Your code here…
ConverterWebPartUserControl myControl =
(ConverterWebPartUserControl)Page.LoadControl(“~/_controltemplates/MyWebPart/MyWebUserControl.ascx”);
this.Controls.Add(myControl);
c- Right-click on the MyWebPart solution and select Rebuild Solution
How to Crawl Open Document Text (odt) files using SharePoint Server 2010?
How to Crawl Open Document Text (odt) files using SharePoint Server 2010?
Open Document Text files can be created by IBM Lotus Symphony. SharePoint Server 2010 can crawl this file types by registering StarOffice/OpenOffice IFilter .
We can download StarOffice/OpenOffice IFilter from this site http://www.ifiltershop.com/sofilter.html
Installation Instructions
Setup file is a self-extracting archive that must be downloaded and opened on the machine where you wish to use StarOffice/OpenOffice IFilter.
- Stop all appropriate Search services.
- Uninstall any previous version of StarOffice/OpenOffice IFilter.
- Start setup file and follow the on-screen instructions.
- Start all appropriate Search services.
- Re-index catalogs containing OpenOffice Writer, Math, Impress, Draw and Calc files.
Additional Setup Steps
Some Microsoft Search products require additional setup steps as described below:
SharePoint Server 2010:
- In SharePoint Central Administration go to “General Application Settings” page
- In the “Search” section click on “Farm-Wide Search Administration”
- Click on ” Search Service Application” link
- On the left side menu select “File Types”
- Make sure that “.odt”, “.odp” and all other StarOffice/OpenOffice file types you are planning to index are included

comparison between Search Technologies capabilities for SharePoint 2010
How to Transfer a SharePoint web part Zone into tabs??
How to Transfer a SharePoint web part Zone into tabs??
I do quite a bit of design and implementation on the SharePoint platform. Today, I created a very handy little script that I think might be something worth sharing. I don’t often post anything so specific on my blog, but I found this to be extremely useful, and I hope you do too.
What is it?
This all started with a great idea from the mind of Matthew Koon. If you’re not familiar with SharePoint, one thing you can do in the platform is place web parts on a page, which are akin to sidebar widgets in WordPress or other CMS platforms. Web parts have a lot of nifty drag-and-drop functionality, but the appearance of them is pretty much limited to what you can do with a bit of CSS and maybe some background images. The script that I created transforms a particular “web part zone,” which contains individual web parts, into a jQuery UI tab control. For each web part in the zone, you see an interactive “tab” instead of a boring static box. The contents of each tab is the contents of the web part, itself.
What does it do?
When you’re editing a page, you’ll see this:
When you publish the page, you’ll see this:
1. Attach Required Scripts
You’ll need both jQuery 1.4.2 and jQuery UI 1.8.5 (or later).
<script type=”text/javascript” src=”http://ajax.googleapis.com/ajax/libs/jquery/1.4.2/jquery.min.js”></script>
<script type=”text/javascript” src=”http://ajax.googleapis.com/ajax/libs/jqueryui/1.8.5/jquery-ui.min.js”></script>
2. Attach the Script
Paste this into an attached JavaScript file:
(function($){
$.fn.wpTabify = function(){
if($(‘.ms-WPAddButton’).size() == 0){
return this.each(function(i){
var tabList = $(‘<ul/>’);
var panels = $(‘<div/>’);
$(this).find(‘.s4-wpTopTable,td[id^=”MSOZoneCell_”] > table’).each(function(j){
$(tabList).append(‘<li><a href=”#ui-tab-panel’ + i + j + ‘”>’ + $(this).find(‘h3.ms-WPTitle’).text() + ‘</a></li>’);
var thisPanel = $(‘<div id=”ui-tab-panel’ + i + j + ‘” class=”wpt-ui-tabs-panel”/>’);
var panelContents = $(this).detach();
$(thisPanel).append($(panelContents).find(‘.ms-WPBody’).html());
$(panels).append(thisPanel);
});
if($(tabList).find(‘li’).size() > 0){
$(this).prepend(panels);
$(this).prepend(tabList);
$(this).tabs();
}
});
}
else{
return false;
}
};
})(jQuery);
3. Wrap Your Web Part Zone
In your custom page layout, place a <div/> tag around a web part zone, and give it a class name or ID of your choosing.
<div>
<WebPartPages:WebPartZone id=”zone1″ runat=”server” title=”Tabs Zone”><ZoneTemplate></ZoneTemplate></WebPartPages:WebPartZone>
</div>
4. Run the Script
Now that you’ve attached the script, run it using a jQuery selector that matches the <div> you created in step three (above). This code also goes in an attached JavaScript file.
$(document).ready(function(){
$(‘.my-web-part-tabs‘).wpTabify();
});
5. Add Some Style (Optional)
You may choose to add a bit of style to your newly tabified web parts (this is not specific to this plug-in, these are just some generic jQuery tabs styles):
.ui-tabs-nav {
margin: 0;
padding: 0;
}
.ui-tabs-nav li {
list-style: none;
margin: 0 1px 0 0;
padding: 0;
float: left;
}
.ui-tabs-nav a {
position: relative;
top: 1px;
display: block;
padding: 10px 8px;
border: solid #e1e0dc;
border-width: 1px 1px 0 1px;
background: #d6d6d6;
color: #999;
text-decoration: none;
-webkit-border-top-left-radius: 5px;
-webkit-border-top-right-radius: 5px;
-moz-border-radius-topleft: 5px;
-moz-border-radius-topright: 5px;
border-top-left-radius: 5px;
border-top-right-radius: 5px;
}
.ui-tabs-nav li.ui-tabs-selected a {
color: #c70d37;
background: #fff;
}
.ui-tabs-panel {
clear: both;
padding: 20px;
background: #fff;
border: 1px solid #e1e0dc;
}
.ui-tabs-hide {
display: none;
}
References:-
Configuring claims and forms based authentication for use with an ASP.NET Membership Provider in SharePoint 2010
Forms Based Authentication
1- Create web application
- Select Claims Based Authentication
- Identity Providers
- Check the Enable Windows Authentication box or you won’t be able to crawl the site
- Check the Enable ASP.NET Membership and Role Provider checkbox
* In the Membership provider name edit box, type SqlMember
* In the Role provider name edit box, type SqlRole - Create a new site collection
2 – Create Database (aspnetdb) for users:
- Navigate to C:\Windows\Microsoft .Net\Framework64\v2.0.50727. Locate the aspnet_regsql.exe application and execute it. This will open the windows in the figure below
- Click next and choose “Configure SQL server for application services
- Click next and enter server name and authentication and click next and verify the server information
- By this you created the aspnetdb now, Now you can populate the SQL Server database with user
- Click next and enter server name and authentication and click next and verify the server information
- By this you created the aspnetdb now, Now you can populate the SQL Server database with user information using an application on CodePlex called MembershipSeeder (http://cks.codeplex.com/releases/view/7450#DownloadId=19598). You can proceed with the configuration without usingthe MembershipSeeder application but you will have to manually add users to the aspnetdb tables
1- Adjust Central Administration web.config
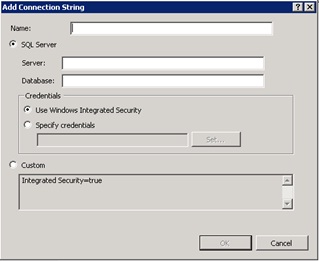
- Add connection string
- Locate central administration from IIS and choose Connection String
- Add New Connection String and enter server information and enter “AspNetSqlMembershipProvider” for the connectionString Name
- Add Member and Role
- Open Central administration web.config
- Locate <system.web> entry and paste the following
-
<roleManager enabled=”true”
cacheRolesInCookie=”false”
cookieName=”.ASPXROLES”
cookieTimeout=”30″z
cookiePath=”/”
cookieRequireSSL=”false”
cookieSlidingExpiration=”true”
cookieProtection=”All”
defaultProvider=”AspNetWindowsTokenRoleProvider”
createPersistentCookie=”false”
maxCachedResults=”25″>
<providers>
<clear />
<add connectionStringName=”AspNetSqlMembershipProvider”
applicationName=”/”
name=”SqlRole”
type=”System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a” /><add applicationName=”/”
name=”AspNetWindowsTokenRoleProvider”
type=”System.Web.Security.WindowsTokenRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a” /></providers>
</roleManager>
<membership defaultProvider=”SqlMember”
userIsOnlineTimeWindow=”15″ hashAlgorithmType=””>
<providers>
<clear />
<add connectionStringName=”AspNetSqlMembershipProvider”
enablePasswordRetrieval=”false”
enablePasswordReset=”true”
requiresQuestionAndAnswer=”true”
passwordAttemptWindow=”10″
applicationName=”/”
requiresUniqueEmail=”false”
passwordFormat=”Hashed”
name=”SqlMember”
type=”System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a” /></providers>
</membership>
- Double check whether the <membership> and <rolemanager> entries only exist ones. Delete any double entries
- Locate the <PeoplePickerWildcards> entry and paste the following below it
<clear />
<add key=”AspNetSqlMembershipProvider” value=”%” />
<add key=”SqlMember” value=”%”/>
<add key=”SqlRole” value=”%”/>
4- Adjust web.config of Security Token Service under Sharpoint WebServices
- Add Connection String
- Locate Security Token Service from IIS and choose Connection Strings
- Add New Connection String and enter server information and enter “AspNetSqlMembershipProvider” for the connectionString Name
- Add Role and manager
- Open STS web.config
- Add a <system.web> entry directly below the </connectionStrings> and enter the following XML
<membership>
<providers>
<add connectionStringName=”AspNetSqlMembershipProvider”
enablePasswordRetrieval=”false”
enablePasswordReset=”true”
requiresQuestionAndAnswer=”true”
passwordAttemptWindow=”10″
applicationName=”/”
requiresUniqueEmail=”false”
passwordFormat=”Hashed”
name=”SqlMember”
type=”System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a” />
</providers>
</membership>
<roleManager enabled=”true”>
<providers>
<add connectionStringName=”AspNetSqlMembershipProvider”
applicationName=”/”
name=”SqlRole”
type=”System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a” />
</providers>
</roleManager>
- Add a </system.web> entry below it
1- Adjust the web.config of the claims based web application.
- Add Connection String
- Locate Security Web application from IIS and choose Connection Strings as before.
- Add New Connection String and enter server information and enter “AspNetSqlMembershipProvider” for the connectionString Name as before.
- Locate the <membership> entry
- Replace everything from <membership> to </membership> with the following XML
<membership defaultProvider=”i”
userIsOnlineTimeWindow=”15″
hashAlgorithmType=””>
<providers>
<clear />
<add connectionStringName=”AspNetSqlMemberShipProvider”
enablePasswordRetrieval=”false”
enablePasswordReset=”true”
requiresQuestionAndAnswer=”true”
passwordAttemptWindow=”10″
applicationName=”/”
requiresUniqueEmail=”false”
passwordFormat=”Hashed”
name=”SqlMember”
type=”System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a” />
<add name=”i”
type=”Microsoft.SharePoint.Administration.Claims.SPClaimsAuthMembershipProvider,
Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c” />
</providers>
</membership>
-
- Locate the <roleManager> entry
- Replace everything from <roleManager> to </roleManager> with the following XML
<roleManager enabled=”true”
cacheRolesInCookie=”false”
cookieName=”.ASPXROLES”
cookieTimeout=”30″
cookiePath=”/”
cookieRequireSSL=”false”
cookieSlidingExpiration=”true”
cookieProtection=”All”
defaultProvider=”c”
createPersistentCookie=”false”
maxCachedResults=”25″>
<providers>
<clear />
<add connectionStringName=”AspNetSqlMemberShipProvider”
applicationName=”/”
name=”AspNetSqlRoleProvider”
type=”System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a” />
<add applicationName=”/”
name=”SqlRole”
type=”System.Web.Security.WindowsTokenRoleProvider, System.Web, Version=2.0.0.0,
Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a” />
<add name=”c” type=”Microsoft.SharePoint.Administration.Claims.SPClaimsAuthRoleProvider,
Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c” />
</providers>
</roleManager>
- Paste the following XML below the PeoplePickerWildcards entry
<clear />
<add key=”AspNetSqlMembershipProvider” value=”%” />
<add key=”SqlMember” value=”%”/>
<add key=”SqlRole” value=”%”/>
6- Add a user policy to the web application
- Go to Central Administration
- Go to Application Management
- Click on Manage Web Applications
- Select the claims based web application
- Click on User Policy
- Click on the Add Users link
- Click the Next button.
- Click the Address Book icon.
- Type in the NT login name or account name and click the search button. If it’s working correctly you should see at least two entries for the account – one that is for the user’s Active Directory account, and one that is for that same account but which was found using the LDAP provider.
- Select the account in the User section and click the Add button
- Click the OK button
- Check the Full Control checkbox, then click the Finish button
Configuring claims and forms based authentication for use with an LDAP provider in SharePoint 2010
Configuring claims and forms based authentication for use with an LDAP provider in SharePoint 2010
Using an LDAP provider with forms based authentication means that users will use their Windows or AD account to log in. However, because forms based authentication will be used they don’t get the usual popup, but they will use a sign-in page to log in.
How to set up forms based authentication while using an LDAP provider?
When you want to create your web application:-
1) Select Claims Based Authentication and Identity Providers: –
* Check the Enable Windows Authentication box or you won’t be able to crawl the site
* Check the Enable ASP.NET Membership and Role Provider checkbox
– In the Membership provider name edit box, type LdapMember.
– In the Role provider name edit box, type LdapRole.

2) Create a new site collection.
3) Adjust the web.config of the Central Administration site:-
* Open the Central Administration site’s web.config file
* Find the entry
<membership>
<providers>
<add name=”LdapMember”
type=”Microsoft.Office.Server.Security.LdapMembershipProvider,
Microsoft.Office.Server, Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c”
server=”SERVER NAME”
port=”389″
useSSL=”false”
userDNAttribute=”distinguishedName”
userNameAttribute=”sAMAccountName”
userContainer=”OU=SPUsers,DC=sharepoint,DC=com”
userObjectClass=”person”
userFilter=”(ObjectClass=person)”
otherRequiredUserAttributes=”sn,givenname,cn” />
</providers>
</membership>
<roleManager enabled=”true” defaultProvider=”AspNetWindowsTokenRoleProvider” >
<providers>
<add name=”LdapRole”
type=”Microsoft.Office.Server.Security.LdapRoleProvider,
Microsoft.Office.Server, Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c”
server=” SERVER NAME”
port=”389″
useSSL=”false”
groupContainer=”OU=SPUsers,DC=sharepoint,DC=com”
groupNameAttribute=”cn”
groupNameAlternateSearchAttribute=”samAccountName”
groupMemberAttribute=”member”
userNameAttribute=”sAMAccountName”
dnAttribute=”distinguishedName”
groupFilter=”(ObjectClass=group)”
userFilter=”(ObjectClass=person)”
scope=”Subtree” />
</providers>
</roleManager>
Note:
The user and group containers are the containers in AD where the users and groups you want to use for authentication reside:-
• Go to the domain controller
• Open Active Directory Users and Computers
• Select a user or a group in the container
• Right click and select All Tasks => Resultant Set Of Policy (Planning)
• Click the browse button next to Container and select the container
• This will give you the path to the container
4) Check whether the and entries only exist ones. Delete any double entries.
5) Edit the entry
<clear /> <add key="AspNetSqlMembershipProvider" value="%" /> <add key="LdapMember" value="*"/> <add key="LdapRole" value="*"/>
6) Adjust the web.config of the Security Token Service (STS) virtual directory:-
* Open the Security Token Service (STS) virtual directory’s web.config file
* Find the entry
* Add a </system.web> entry directly below it
<membership>
<providers>
<add name=”LdapMember”
type=”Microsoft.Office.Server.Security.LdapMembershipProvider,
Microsoft.Office.Server, Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c”
server=”SERVER NAME”
port=”389″
useSSL=”false”
userDNAttribute=”DISTINGUISHEDNAME”
userNameAttribute=”SAMACCOUNTNAME”
userContainer=”OU=SPUSERS,DC=SHAREPOINT,DC=COM”
userObjectClass=”person”
userFilter=”(ObjectClass=person)”
otherRequiredUserAttributes=”SN,GIVENNAME,CN” />
</providers>
</membership>
<roleManager enabled=”true”>
<providers>
<add name=”LdapRole”
type=”Microsoft.Office.Server.Security.LdapRoleProvider,
Microsoft.Office.Server, Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c”
server=” SERVER NAME”
port=”389″
useSSL=”false”
groupContainer=”OU=SPUSERS,DC=SHAREPOINT,DC=COM”
groupNameAttribute=”cn”
groupNameAlternateSearchAttribute=”SAMACCOUNTNAME”
groupMemberAttribute=”member”
userNameAttribute=”SAMACCOUNTNAME”
dnAttribute=”DISTINGUISHEDNAME”
groupFilter=”(ObjectClass=group)”
userFilter=”(ObjectClass=person)”
scope=”Subtree” />
</providers>
</roleManager>
*Add a </system.web> entry directly below it
7) Adjust the web.config of the claims based web application
* Locate the <Providers> entry
* Edit the following XML directly below the entry
<add name=”LdapMember”
type=”Microsoft.Office.Server.Security.LdapMembershipProvider,
Microsoft.Office.Server, Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c”
server=” SERVER NAME”
port=”389″
useSSL=”false”
userDNAttribute=”DISTINGUISHEDNAME”
userNameAttribute=”SAMACCOUNTNAME”
userContainer=”OU=SPUSERS,DC=SHAREPOINT,DC=COM”
userObjectClass=”person”
userFilter=”(ObjectClass=person)”
otherRequiredUserAttributes=”SN,GIVENNAME, CN” />
* Edit <roleManager> the entry
<add name=”LdapRole”
type=”Microsoft.Office.Server.Security.LdapRoleProvider,
Microsoft.Office.Server, Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c”
server=” SERVER NAME “
port=”389″
useSSL=”false”
groupContainer=”OU=SPUsers,DC=sharepoint,DC=com”
groupNameAttribute=”cn”
groupNameAlternateSearchAttribute=”samAccountName”
groupMemberAttribute=”member”
userNameAttribute=”sAMAccountName”
dnAttribute=”distinguishedName”
groupFilter=”(ObjectClass=group)”
userFilter=”(ObjectClass=person)”
scope=”Subtree” />
8) Edit the <PeoplePickerWildcards> entry
<clear /> <add key="AspNetSqlMembershipProvider" value="%" /> <add key="LdapMember" value="*"/> <add key="LdapRole" value="*"/>
9) Add a user policy to the web application
* Go to Central Administration
* Go to Application Management
* Click on Manage Web Applications
* Select the claims based web application
* Click on User Policy
* Click on the Add Users link
* Click the Next button.
* Click the Address Book icon.
* Type in the NT login name or account name and click the search button. If it’s working correctly you should see at least two entries for the account – one that is for the user’s Active Directory account, and one that is for that same account but which was found using the LDAP provider.
* Select the account in the User section and click the Add button
* Click the OK button
* Check the Full Control checkbox, and then click the Finish button.
http://blogs.technet.com/b/speschka/archive/2009/11/05/configuring-forms-based-authentication-in-sharepoint-2010.aspx
http://kbochevski.blogspot.com/2011/01/setup-fba-for-sharepoint-2010-using-vs.html
change service accounts and service account passwords in SharePoint Server 2007
How to change service accounts and service account passwords in SharePoint Server 2007 and in Windows SharePoint Services 3.0
To change the passwords for service accounts in Microsoft office SharePoint server 2007 and in Microsoft Windows SharePoint Services 3.0, we need to do steps with stsadmin commands and through Central Administration Web Site.
Let us do simulation with complete example, the following table contains farm servers
| Server Name | Server Role |
| WebFront1 | Webfrontend server, Query Server |
| WebFront2 | Webfrontend server, Query Server |
| Index1 | Host Central Administration Site, Indexer |
| SQL1 | Clustered Database |
| SQL2 |
We need to change the password for accounts that run central administration service, office SharePoint search service, and SSP.
As I mentioned in the above table, Index 1 server hosts (central administration role), also play as indexer. So we need to update services account password as the following:-
1- Update the password for the account that is used by the Central Administration application pool. To do this, follow these steps:
a- On all servers in the server farm, open a command prompt, type the following line, and then press ENTER:
cd %commonprogramfiles%\Microsoft Shared\Web server extensions\12\Bin
b- On the server that hosts the Central Administration Web site, type the following line at the command prompt, and then press ENTER:
stsadm -o updatefarmcredentials -userlogin DomainName\UserName -password NewPassword
c- On all other servers in the server farm, type the following line at the command prompt, and then press ENTER:
stsadm -o updatefarmcredentials -userlogin DomainName\UserName -password NewPassword -local
d- Restart Microsoft Internet Information Services (IIS) 6.0. To do this, type the following line at the command prompt, and then press ENTER:
iisreset /noforce
2- Verify that the Administration Application Pool Credential Deployment job definition is no longer displayed on the Timer Job Definitions page of SharePoint 3.0 Central Administration. To do this, follow these steps:
a- Open SharePoint 3.0 Central Administration, click Operations, and then click Timer job definitions under Global Configuration.
b- Verify that the Administration Application Pool Credential Deployment job definition is no longer displayed in the list.
Note If the Administration Application Pool Credential Deployment job definition is displayed in the list, wait until it disappears from the list.
WebFront1 and WebFront2 servers play Query Role and hosts web applications . So we need to update the password of the application pool account that is used by Web applications on the server farm, the password for the account that is used by every Shared Services Provider (SSP) on the server farm, and for the account that is used to run the Office SharePoint Server Search service as the following:-
1- Update the password for the application pool account that is used by Web applications on the server farm. To do this, type the following line at a command prompt on every server on the server farm, and then press ENTER:
stsadm -o updateaccountpassword -userlogin DomainName\UserName -password NewPassword –noadmin
2- Update the password for the account that is used by every Shared Services Provider (SSP) on the server farm. To do this, type the following line at a command prompt on every server on the server farm, and then press ENTER:
stsadm.exe -o editssp -title SharedServicesProviderName -ssplogin DomainName\UserName -ssppassword NewPassword
3- Update the password for the account that is used to run the Office SharePoint Server Search service. To do this, type the following line at the command prompt, and then press ENTER:
stsadm.exe -o osearch -farmserviceaccount DomainName\UserName -farmservicepassword NewPassword
4- Update the password for the default content access account that is used by the Office SharePoint Server Search service. To do this, follow these steps:
a- Open SharePoint 3.0 Central Administration, and then click the link to the SSP Web application under Shared Services Administration.
b- Under Search, click Search settings, and then click Default content access account.
c- Specify the password to use for the content access account, and then click OK.
Refernces:-
User and Service Account (Office SharePoint Server)
User and Service Account
There are two types of installation in MOSS2007, standalone installation and server farm installation. According to your installation type selection you need to plan for administrative and service accounts.
Single server standard requirements
In case of, you are deploying to a single server computer, accounts requirements are greatly reduced. You can use a single account for all of the account purposes. In a production environment, ensure that the accounts you create have the appropriate permissions for their purposes.
| Account | Description | Single server standard requirements |
| SQL Server service account | SQL Server prompts for this account during SQL Server Setup. This account is used for the following SQL Server services:§ SQL Server (MSSQLSERVER)§ SQL Server Agent (SQLSERVERAGENT) | Local System account (default) |
| Setup user account | The user account that is used to run:§ Setup on each server computer§ The SharePoint Products and Technologies Configuration Wizard
§ The Psconfig command-line tool § The Stsadm command-line tool |
Member of the Administrators group on the local computer |
| Server farm account | This account is also referred to as the database access account.This account is:§ The identity for the application pool that hosts the SharePoint Central Administration Web site.
§ The process account for the Windows SharePoint Services Timer service. |
Network Service (default)No manual configuration is necessary. |
| SSP application pool account | Application pool identity for the shared services administration Web application. | No manual configuration is necessary. |
| SSP service account | Used by the following:§ SSP Web services for inter-server communication§ SSP Timer service to run specific types of jobs
§ Application pool identity of application pool associated with the virtual directory associated with a given SSP |
§ No manual configuration is necessary.§ This account should not be a member of the Administrators group on any computer in the server farm. |
| Office SharePoint Server Search service account | Used as the service account for the Office SharePoint Server Search service. There is only one instance of this service and it is used by all SSPs. | By default, this account runs as the Local System account.§ If you want to crawl remote content by changing the default content access account or by using crawl rules, change this to a domain user account. If you do not change this account to a domain user account, you cannot change the default content access account to a domain user account or add crawl rules to crawl this content. This restriction is designed to prevent elevation of privilege for any other process running as the Local System account. |
| Default content access account | The default account used within a specific SSP to crawl content, unless a different authentication method is specified by a crawl rule for a URL or URL pattern. | No manual configuration is necessary if this account is only crawling local farm content. If you want to crawl remote content by using crawl rules, change this to a domain user account, and apply the requirements listed for a server farm. |
| Content access account | A specific account that is configured to access a content source. This account is optional and is specified when you create a new crawl rule. For example, content sources that are external to Office SharePoint Server (such as a file share) might require a different content access account. | Same as the SSP default content access account listed previously. |
| Profile import default access account | Used to:§ Connect to a directory service, such as the Active Directory directory service, a Lightweight Directory Access Protocol (LDAP) directory, a Business Data Catalog application, or other directory source.§ Import profile data from a directory service.
If no account is specified, the default content access account is used. If the default content access account does not have read access to the directory or directories that you want to import data from, use a different account. You can plan up to one account per directory connection. |
§ Read access to the directory service.§ If Enable Server Side Incremental is selected for an Active Directory connection and the environment is Windows 2000 Server, the account must have the Replicate Changes permission in Active Directory. This permission is not required for Windows Server 2003 Active Directory environments.§ Manage User Profiles personalization services permission.
View permissions on entities used in Business Data Catalog import connections. |
| Excel Services unattended service account | The account that Excel Calculation Services uses to connect to external data sources that require a non-Windows user name and password string for authentication. If this account is not configured, Excel Services will not attempt to connect to these types of data sources. Although the account credentials are used to connect to non-Windows data sources, the account must be a member of the domain in order for Excel Calculation Services to use it. | Must be a domain user account. |
| Windows SharePoint Services Search service account | Used as the service account for the Windows SharePoint Services Help Search service. There is only one instance of this service in a farm. | By default, this account runs as the Local System account. |
| Windows SharePoint Services Search content access account | Used by the Windows SharePoint Services Search application server role to crawl content across sites. | Must not be a member of the Farm Administrators group.The following are automatically configured:Added to the Web application Full Read policy for the farm. |
| Application pool identity | The user account that the worker processes that service the application pool use as their process identity. This account is used to access content databases associated with the Web applications that reside in the application pool. | No manual configuration is necessary.The Network Service account is used for the default Web site that is created during Setup and configuration. |
Server farm requirements
In case of, you are deploying to more than one server computer use the server farm standard requirements to ensure that accounts have the appropriate permissions to perform their processes across multiple computers.
| Account | Description | Server farm standard requirements |
| SQL Server service account | SQL Server prompts for this account during SQL Server Setup. This account is used for the following SQL Server services:§ SQL Server (MSSQLSERVER)§ SQL Server Agent (SQLSERVERAGENT) | Use either a Local System account or a domain user account.If a domain user account is used, this account uses Kerberos authentication by default, which requires additional configuration in your network environment. If SQL Server uses a service principal name (SPN) that is not valid (that is, that does not exist in the Active Directory directory service environment), Kerberos authentication fails, and then NTLM is used. If SQL Server uses an SPN that is valid but is not assigned to the appropriate container in Active Directory, authentication fails, resulting in a “Cannot generate SSPI context” error message. Authentication will always try to use the first SPN it finds, so ensure that there are no SPNs assigned to inappropriate containers in Active Directory.If you plan to back up to or restore from an external resource, permissions to the external resource must be granted to the appropriate account. If you use a domain user account for the SQL Server service account, grant permissions to that domain user account. However, if you use the Network Service or the Local System account, grant permissions to the external resource to the machine account (domain_name\SQL_hostname$). |
| Setup user account | The user account that is used to run:§ Setup on each server computer§ The SharePoint Products and Technologies Configuration Wizard
§ The Psconfig command-line tool § The Stsadm command-line tool |
§ Domain user account.§ Member of the Administrators group on each server on which Setup is run.§ SQL Server login on the computer running SQL Server.
§ Member of the following SQL Server security roles:
If you run Stsadm commands that affect a database, this account must be a member of the db_owner fixed database role for the database. |
| Server farm account | This account is also referred to as the database access account.This account is:§ The identity for the application pool that hosts the SharePoint Central Administration Web site.
§ The process account for the Windows SharePoint Services Timer service. |
§ Domain user account.§ If the server farm is a child farm with Web applications that consume shared services from a parent farm, this account must be a member of the db_ownerfixed database role on the configuration database of the parent farm.Additional permissions are automatically granted for this account on Web servers and application servers that are joined to a server farm.
This account is automatically added as a SQL Server login on the computer running SQL Server and added to the following SQL Server security roles: § dbcreator fixed server role § securityadmin fixed server role db_owner fixed database role for all databases in the server farm |
| SSP application pool account | Application pool identity for the shared services administration Web application. | No manual configuration is necessary.The following are automatically configured:§ Membership in the db_owner role for the SSP content database.
§ Access to read from and write to the SSP content database. § Access to read from and write to content databases for Web applications that are associated with the SSP. § Access to read from the configuration database. § Access to read from the Central Administration content database. Additional permissions to front-end Web servers and application servers are automatically granted. |
| SSP service account | Used by the following:§ SSP Web services for inter-server communication§ SSP Timer service to run specific types of jobs
§ Application pool identity of application pool associated with the virtual directory associated with a given SSP |
§ Use a domain user account.§ No manual configuration is necessary. The same permissions as the SSP application pool account are automatically granted.§ This account should not be a member of the Administrators group on any computer in the server farm. |
| Office SharePoint Server Search service account | Used as the service account for the Office SharePoint Server Search service. There is only one instance of this service and it is used by all SSPs. | § Must be a domain user account.§ Should not be a member of the Farm Administrators group on the server.The following are automatically configured:
§ Access to read from the configuration database. |
| Default content access account | The default account used within a specific SSP to crawl content, unless a different authentication method is specified by a crawl rule for a URL or URL pattern. | § Must be a domain user account.§ Must not be a member of the Farm Administrators group.§ Read access to external or secure content sources that you want to crawl by using this account.
§ For sites that are not a part of the server farm, this account must explicitly be granted Full Read permissions on the Web applications that host the sites. The following are automatically configured: Full Read permissions are automatically granted to content databases hosted by the server farm. |
| Content access account | A specific account that is configured to access a content source. This account is optional and is specified when you create a new crawl rule. For example, content sources that are external to Office SharePoint Server (such as a file share) might require a different content access account. | § Read access to external or secure content sources that this account is configured to access.For Web sites that are not a part of the server farm, this account must explicitly be granted Full Read permissions on the Web applications that host the sites. |
| Profile import default access account | Used to:§ Connect to a directory service, such as the Active Directory directory service, a Lightweight Directory Access Protocol (LDAP) directory, a Business Data Catalog application, or other directory source.§ Import profile data from a directory service.
If no account is specified, the default content access account is used. If the default content access account does not have read access to the directory or directories that you want to import data from, use a different account. You can plan up to one account per directory connection. |
§ Read access to the directory Read access to the directory service.§ If Enable Server Side Incremental is selected for an Active Directory connection and the environment is Windows 2000 Server, the account must have the Replicate Changes permission in Active Directory. This permission is not required for Windows Server 2003 Active Directory environments.§ Manage User Profiles personalization services permission.
View permissions on entities used in Business Data Catalog import connections. |
| Excel Services unattended service account | The account that Excel Calculation Services uses to connect to external data sources that require a non-Windows user name and password string for authentication. If this account is not configured, Excel Services will not attempt to connect to these types of data sources. Although the account credentials are used to connect to non-Windows data sources, the account must be a member of the domain in order for Excel Calculation Services to use it. | Must be a domain user account. |
| Windows SharePoint Services Search service account | Used as the service account for the Windows SharePoint Services Help Search service. There is only one instance of this service in a farm. |
The following are automatically configured:
|
| Windows SharePoint Services Search content access account | Used by the Windows SharePoint Services Search application server role to crawl content across sites. |
The following are automatically configured: Added to the Web application Full Read policy for the farm. |
| Application pool identity | The user account that the worker processes that service the application pool use as their process identity. This account is used to access content databases associated with the Web applications that reside in the application pool. | No manual configuration is necessary.The following are automatically configured:
Additional permissions for this account to front-end Web servers and application servers are automatically granted. |
References:-
http://technet.microsoft.com/en-us/library/cc263445%28office.12%29.aspx#Section2